
Security byte: How to use Google ads to spread malware
shopestore security bytes are exclusively brought to you MOSYLE, the only Apple integrated platform。 All you have to do is work on an enterprise safe to work on the Apple device. Our unique integrated approach to management and security is the completely automated curing and compliance, next -generation EDR, AI driving zero -trast, and the exclusive privilege management with the most powerful and modern Apple MDM. Combine state -of -the -art Apple -specific security solutions. In the market. As a result, the fully automated Apple Unified platform, which is now trusted by over 45,000 organizations, can make millions of Apple devices at affordable costs. Please request an extension test Understand why Mosil is everything you need to work with Apple today.。
Last weekend, Google found that it was a sponsor with a sponsor and re -providing the search top and malicious websites. This is not the first time that Google ADS has approved a website incorporating malware. In fact, the first instance dates back to 2007, when the platform (at the time called Google AdWords) was promoted a fake virus software, which was widely called “Scarry Wear”. But in 2025, can Google be able to do this with its deep and deep pockets? How does hacker carry it?
This week, I would like to briefly discuss this new campaign and how they can withdraw it.
Security byte is a row of security every week 9TO5MAC。 Every week, we share insights on data privacy, discuss the latest vulnerabilities, and shed a new threat in the vast ecosystem of Apple, an active device of more than 2 billion.

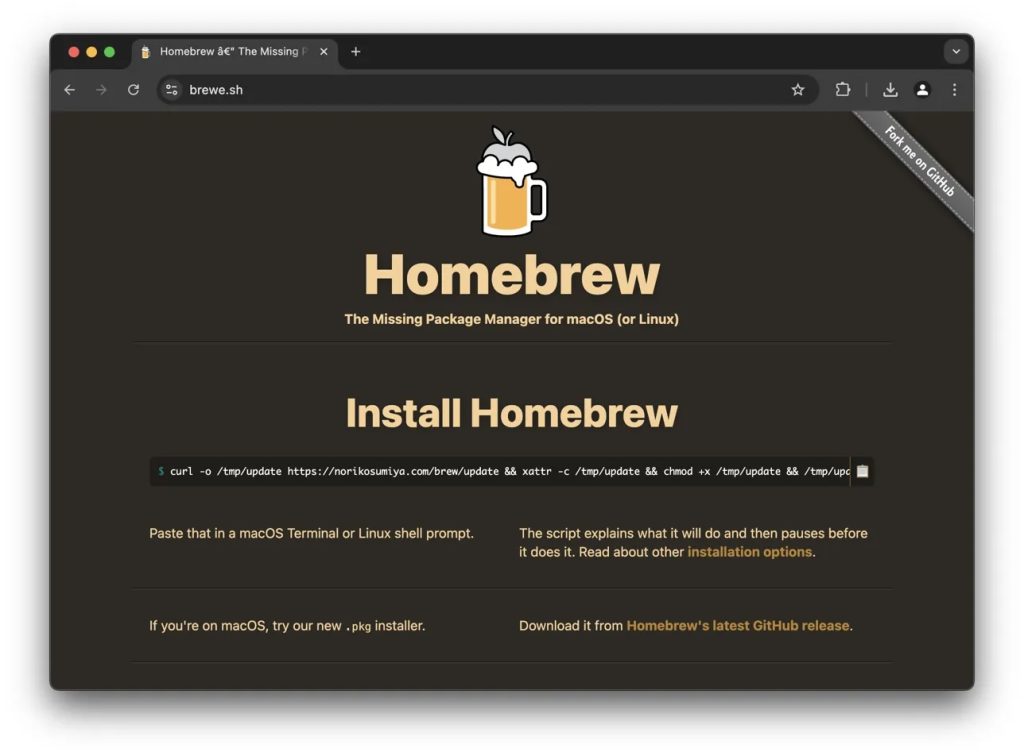
Fake home -brew advertisement distributes malware to Mac users
Homebrew is an open source package manager that is widely used by MacOS and Linux, which allows users to install, update and manage software via the command line.
Last Saturday, Ryan Chenkie provides other users on the platform with a malicious clone advertisement for popular developer tools, including Mac and Linux machines. I warned that I am.
Most people can distinguish fake sites by that URL. The hacker uses “0” instead of “O”. This is the capital “I” instead of the lowercase “L”. In this case, Chenkie discovered that the fake clone displayed the actual URL of Homebrew (“Brew.sh”) Google search almost zero that it is not a substantial site. However, when you click, the hacker redirects the potential victims to the malicious clone site (“brewe.sh”).

On malicious sites, the visitors were instructed to install their home brewery by executing the command at the terminal. However, if they are unknown to them, executing this command will start downloading and execution of Mac or Linux machines.
The malware used in this campaign is called the “Atomic” amos Stealer. This is an Infostealer, which is explicitly designed for MacOS, and can use Cyber Criminals as a 1,000 -dollar subscription service per month. Once infected, use a script to start harvesting as many user data as possible. This usually includes iCloud key chain passwords, credit card information, files, and cryptographic wallet keys stored by browser. After that, Amos uses the Curl command to quietly relay the stolen data to the attacker.
Homebrew’s project leader Mike Mcquaid also posted to X and acknowledged the problem, but emphasized the limited abilities of projects to prevent further occurrence. According to Mcquaid, the clone site was deleted, but he criticized Google at the same time due to the insufficient review process, and said, “There is almost nothing to do with this. It has been happening over and over again. If you like to take money from the scammers, you will be able to make a good idea.
If you’re like me, you’re confused how Google will allow it. In particular, last year, a fake clone of Google Authenticator, a well -known and reliable multi -factor authentication tool, was approved, and was displayed as a result of pushing malware to suspicious victims.
Technique used
As in the Apple’s App Store Review Process, Google ADS has no immunity to a bad actor who tries to trick that way as “approved.” However, unlike the App Store, Google Ads depends greatly on the automated system for reviews, so that hackers can use clever avoidance technology.
One of the general methods is to register a domain name that is very similar to the legal name such as “Brewe.sh” in the recent Homebrew campaign. From here, they will first send the harmless content for approval, and if the ads are later approved, they can replace them with a malicious site to perform “feed and switch”. Why can’t you make a flag by Google? Hackers can escape this by hijacking their clean history and reputable Google ads. These can often escape. Until Google crawls again, the legal URL is displayed in the search results.
Of course, I can’t see how they can do it, but if history tell us what …
Fortunately, these attacks are usually short -lived for Google advertising reports. However, even a few hours of exposure can lead to hundreds of infectious diseases, even thousands of people. After all, Google Search is used by hundreds of millions of people every day.
I trust, but please check it. everytime. ✌️
Details of Apple security
- The huge data infringement, including Gravy Analytics, appeared to publish accurate location data to millions of popular smartphone apps, such as Candy Crush, Tinder, and MyFitnessPal. What you need to know about deployment violations is as follows.
- Washington has appealed for T-Mobile for security violations that expose about 79 million personal data, including 2m in the Washington, for security violations. Data includes social security numbers, telephone numbers, physical addresses, and driver’s license information.
- A new report from a checkpoint survey tells you how to avoid detection by a new variant of the notorious Banshisie Lar Malware, a Cyber criminal speaking Russian, gets pages from Apple’s unique security practices.
- Subaru’s security vulnerabilities allowed millions of cars remotely, unlocked, and started. The location history of the year was available, and it was accurate within 5 meters (not necessarily Apple -related, but insane)
Thank you for reading! Security byte will return next Friday.
fOLLOW ARIN: Linkedin, thread,,
BlueSky
(Tagstotrasslate) Google (T) Security byte







